Learn about “The Java security model”.
The Java security model
The Java security model, introduced in Java 2, is the basis of highly secured and distributed enterprise Java applications. The model is based on a customizable “sandbox” in which Java software programs can run safely, without potential risk to systems or users. Java security technology includes a large set of APIs, tools, and implementations of commonly used security algorithms, mechanisms, and protocols.
The architecture of the Java security model
The Java 2 security platform is formed by two parts: Core Java 2 Security Architecture and Java Cryptography Architecture. These two parts are presented in Figure A. The bottom layer components are the two main parts of the Java 2 security platform, and the top layer consists of the security extensions. Three security extensions were separately available until Java 1.3.1, but starting with Java 1.4, they were integrated into J2SE.

Core Java 2 Security Architecture
This is a part of the Java platform, and it includes the byte code verifies, class loader, security manager, access controller, access rights facilities, policy description tools, and so on. Here’s a look at the process of Java code execution in Core Java 2 Security Architecture components.
The byte code verifier checks to see if the Java code conforms to the Java Language Specification. There are two steps to this task: (1) The byte code verifier analyzes the byte code sequence; (2) The byte code verifier checks references to other classes. For example, if a class accesses another class’ method, the byte code verifier checks if it declared as public.
Typical operations of byte code verifier check to see: if the byte code begins with the 0xCAFEBABE sequence; if there are lost bytes; if final classes have subclasses (they should not); what types of method arguments there are, and so on.If everything is okay, class loader translates byte code into Java classes, which are then operated by JVM. Class loaders also ensure that untrusted code cannot interfere with the running of other Java programs. There can be defined different policies to hint if a particular class needs to be loaded. Class loader and Java standard classes can also define if access to particular system resources is allowable for a class by delegating to Security Manager decision rights.
Security Manager is a special class that can be implemented by developer; it points out if a class can access a given resource (e.g., file access or network connection). To make such a decision the Security Manager analyzes the source of the request. If access is denied, java.lang.SecurityException is generated; otherwise, a call is handled in the usual way. (A future article will explain how to create a custom Security Manager.)
In order to increase flexibility, an application can use another special mechanism called Access Controller. The Java platform provides additional low-level security features like automatic memory management and strong data typing. This leads to a more robust code and reduces memory corruption and the possibility of vulnerabilities. Access rights control is the most important enhancement in the Java 2 security system. The java.security package contains classes and interfaces that form the Core Java 2 Security Architecture.
Java Cryptography Architecture (JCA)
It provides the infrastructure for executing the main cryptographic services in the Java platform, including digital signatures, message digests, ciphers, message authentication codes key generators, and key factories. JCA also ensures data integrity and provides APIs for all listed features.
JCA is a part of built-in Java packages related to the Java security platform, but it is separate because of its service-oriented nature. Generally speaking, JCA is just an interface, and there can be many implementations for this interface. Sun Microsystems provides its own implementation of JCA starting with Java 1.4, and it is fully integrated into the standard Java package. It supports a wide range of standard algorithms including RSA, DSA, AES, Triple DES, SHA, PKCS#5, RC2, and RC4. JCA is an extensible, full featured API for building secure applications. It is also algorithm and implementation independent and uses provider-based (pluggable) architecture.
Extensions
The Java platform includes a number of built-in providers that implement a basic set of security services that are widely used today. However, some applications may rely on emerging standards not yet implemented, or on proprietary services.The Java platform supports the installation of
custom providers that implement such services. Java Cryptographic Extension, Java Secure Socket Extension, and Java Authentication and Authorization Service are the main components of such pluggable interoperability.
Java Cryptographic Extension (JCE)
This is a Sun Microsystems extension for ciphering and deciphering data blocks and is a part of JCA implementation. JCE was made a Java extension as a conditional of U.S. encryption technologies’ export conditions to third-party countries.
Java Secure Socket Extension (JSSE)
The Secure Sockets Layer (SSL) has become the most widely used data protocol with supported data integrity through encryption. JSSE is a standard interface and reference implementation of the SSL protocol. A developer can use another commercial SSL implementation, but common JSSE interfaces can still be used. The modern Java platform contains other secure socket protocols, including Transport Layer Security (TLS), Kerberos, and the Simple Authentication and Security Layer (SASL). JSSE also includes full support of HTTPS over SSL/TLS.
Java Authentication and Authorization Service (JAAS)
This implements access limiting based on user authentication. Together with Access Control, it provides abstract authentication APIs that incorporate a wide range of login mechanisms through a pluggable architecture. It also provides a comprehensive policy and permissions API that allows a developer to create and administer applications requiring fine-grained access to security-sensitive resources. A main feature is that it enables single sign-on of multiple authentication mechanisms and fine-grained access to resources based on the identity of the user or code signer.
Recent support for time stamped signatures (starting with Java 5) makes it easier to deploy signed code by avoiding the need to re-sign code when the signer’s certificate expires.
The Top 10 of Internet Security Threat
Let’s start with having a look at some of the trends that have emerged during this period.
1. Data theft, data leakage and confidential information theft for financial gains has emerged as the top most threat.
2. The attackers are consolidating their assets, like bots, trojans, worms, to make a coordinated network of criminal activities.
3. Usage of medium severity attacks, which does not result in an immediate effect, to first enter the system quietly and subsequently launching more powerful attacks in a consolidated manner.
4. Emergence of “Underground Economy Servers”, which are used by criminals to sell stolen information. The hub of these servers is U.S. with 51% servers located there.
The Top 10 of Internet Security Threat
1. Government sector topped the number of data breaches, potentially leading to identity theft, accounting for 25% of the total.
2. Microsoft Internet Explorer topped in all browser targeted attacks with 77% contribution.
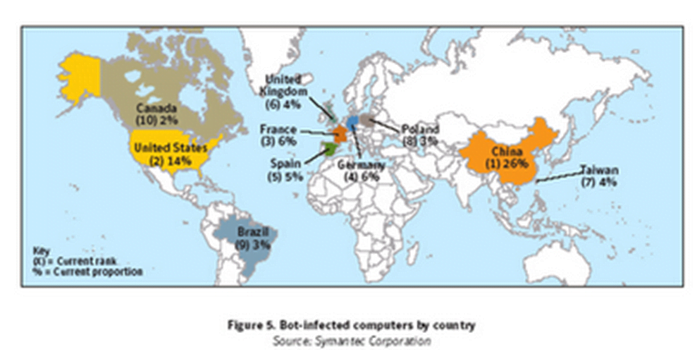
3. China tops with the maximum bot-infected computers in the world, a whopping 26% of the worldwide total.
4. In cities, Beijing tops with just over 5% bot-infected computers of the worldwide total.
5. Israel tops the malicious activity per Internet user list.
6. SMTP tops the list for propagation mechanism with 78% of the malicious code being spread using it.
7. In databases, Oracle has 168 vulnerabilities documented by Symantec which is more than any other database.
8. Financial services sector tops with 30% of the total spam being related to it.
9. MSN Messenger with 35% tops the categories of new messaging threats.
10. Last but the biggest, Home Users accounted for 93% of all the attacks making it to the top in all user categories.
The U.S. Scenario of Internet Security Threat
According to the report, U.S. tops in 5 out of 6 kinds of malicious activities as depicted in the table below. This does not come as a surprise as U.S. comprises of 19% of the world’s Internet population, has such a large Internet infrastructure with a steady growth in broadband user base. This provides more opportunities for attackers to spread malicious activity. Below are some of the highlights specific to U.S. Internet scenario.
1. With 33% attacks originating out of U.S., it is the top most country in worldwide attacking activities.
2. It has the highest number of bot command and control computers with 40% of the world’s total.
3. The U.S. accounted for 31% of all malicious activities which is more than any other country.
4. Out of all debit and credit cards for sale on underground economy servers, 86% were issued by banks in U.S.
5. Nearly half of the world’s spam originated in U.S. with 44% of the worldwide total.
The future Trends
1. Windows Vista with its public release in 2007, expected to be adopted largely, might see an exploitation of vulnerabilities by the attackers.
2. Third-party applications which do not go through a proper Security Development Lifecycle will become more susceptible to threats because of their large user base.
3. New channels for phishing will emerge like Massively Multiplayer Online Games (MMOG). New methods like “Intelligence Lead Phishing” made possible by compromising a database of a social network, will lead to more targeted phishing activity. With high degree of personalization , this will increase the probability of user being exploited.
4. SMiShing – Spam and Phishing will go mobile. Simply because of the size of the user base and the user’s perception of SMS/MMS being more personal will attract more attackers to this segment.
5. Software Virtualization which allows one computer(host) to run other computers (guests) will see an increase in threats in which the guest system can potentially be used to break into the host system causing damages and data theft. Symantec accepts that this is a relatively new area and require more in-depth analysis.
It is in our personal interest to be knowledgeable about the prevalent security threats so that we can protect our personal information from being compromised. Simply put, prevention is better than cure. Since Home Users’ (Consumers) segment is the target of 93% attacks, we should be taking necessary actions to safeguard ourselves against the same.
Best Practices for Users
1. You should use a comprehensive and latest Internet security solution combining antivirus, firewall, intrusion detection, and vulnerability management.
2. Ensure that security patches are up to date
3. Keep your passwords are a mix of letters and numbers, and change them often.
4. Never view, open, or execute any email attachment unless the attachment is from a trusted source.
5. Never disclose any confidential personal or financial information to a source which is not known or trusted.
6. Beware of programs that flash ads in the user interface; this could be a Spyware.
7. Report the potential malicious activities.
If the Internet has to grow to its full potential, we will need to find ways to protect the users from such threats which come as obstacles in widespread adoption of Internet for business as well as personal use.